Applies to Software Auditing, Database Auditing, Database Application Auditing, Oracle 12c.
Key features of Oracle 12c Security are Auditing, Privileges, Data Redaction, Database Vault.
We will discuss about Auditing in more detail. Privileges, Data Redaction, and Database Vault will be discussed as separate blogs.
Let's see what features are available in existing Oracle releases up to Oracle 11g Release 2.
There are different types of Auditing that you can perform at Oracle Database level. In general, auditing is performed to keep safe Database and to have better user control. It can also be used monitor any activities at Database level. For example: To monitor suspicious activity. At Database parameter level, we can use AUDIT_TRAIL, AUDIT_SYS_OPERATIONS and use package DBMS_FGA.ADD_POLICY for fine grained auditing.
Where Audits are Stored?
How Audit Data are Secured?
Audits are secured within the Oracle database at syslog audit: AUDIT_SYSLOG_LEVEL= local1.info
and by using Oracle Audit Vault.
EAI is from SYS object view (SYS.UNIFIED_AUDIT_TRAIL) that has columns like FGA_POLICY_NAME, DP_TEXT_PARAMETERS1, DP_BOOLEAN_PARAMETERS1, RMAN_OPERATION, RMAN_OBJECT_TYPE, RMAN_DEVICE_TYPE, RMAN_xxx, OLS_POLICY_NAME, OLS_xxx, DV_xxx
Audit policy can be created at RMAN level by flushing the audit data using object SYS.DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL.
Oracle Label Security (OLS)
Real Application Security (RAS)
Audit policy can be using component OLS.
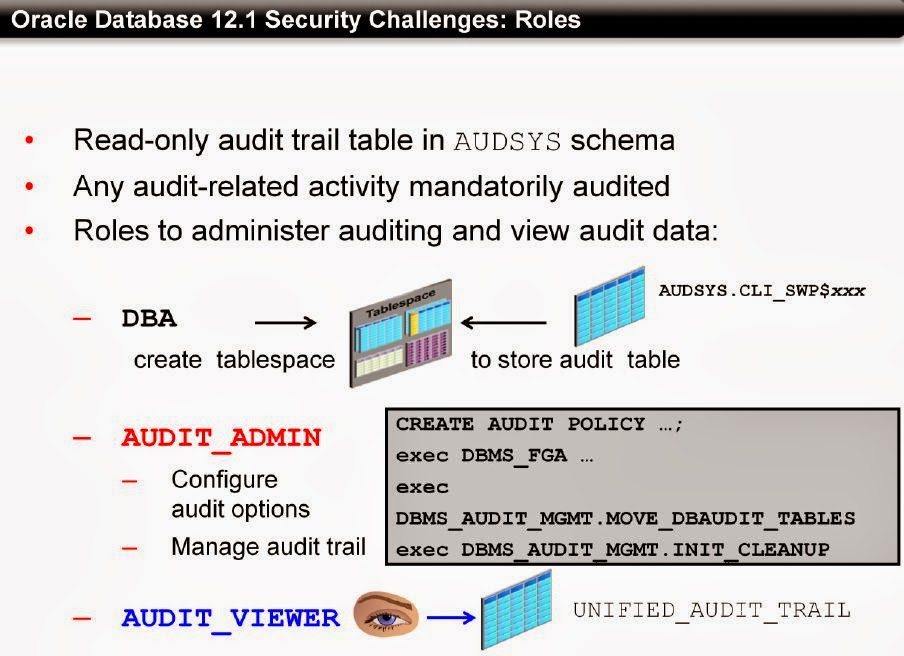
Packages like DBMS_AUDIT_MGMT can assist with AUDIT_ADMIN (Audit Administration) challenges. AUDIT_VIEWER can get UNIFIED_AUDIT_TRAIL views. AUDSYS is a dedicated schema at Database level.
Using 'Create Audit Policy' command, you can also create object-specific actions such as LOCK on a specific table or executing a grant on a specific object (For example: PL/SQL Procedure or Package).
Using 'Create Audit Policy' command, you can also add Conditions and Evaluations per session, statement and instance basis. Actions e.g., RENAME, ALTER on a particular Table.
Commonly used auditing requirements are done for compliance and certifications reasons. Regulatory bodies with common auditing requirements:
Sarbanes-Oxley Act (SOX)
Health Insurance Portability and Accountability Act (HIPAA)
Financial Services Agency (FSA)
Payment Card Industry (PCI)
Data Security Standard (DSS)
Personally Identifiable Information (PII)
International Convergence of Capital Measurement and Capital Standards: a Revised Framework (Basel II) (ICCM) (BCBS)
Bank for International Settlements (BIS)
Japan Privacy Law / Japanese Hitoshi
Japanese Requirement Sarbanes-Oxley Act Section 302 (JSOX) Management Certification
European Union Directive on Privacy and Electronic Communications EU (DPEC)
1. Oracle Database 2 Day + Security Guide
12c Release 1 (12.1)
E17609-15
Chapter 9 Auditing Database Activity
http://docs.oracle.com/cd/E16655_01/server.121/e17609/tdpsg_auditing.htm
2. Oracle Database Security Guide
12c Release 1 (12.1)
E17607-19
Chapter 21 Introduction to Auditing
and
Chapter 22 Configuring Audit Policies
http://docs.oracle.com/cd/E16655_01/network.121/e17607/auditing.htm
3. Security Inside Out, Plug into Defense-in-Depth with Oracle Database 12c
https://blogs.oracle.com/securityinsideout/entry/plug_into_defense_in_depth
https://blogs.oracle.com/securityinsideout/
Key features of Oracle 12c Security are Auditing, Privileges, Data Redaction, Database Vault.
We will discuss about Auditing in more detail. Privileges, Data Redaction, and Database Vault will be discussed as separate blogs.
1. Auditing Overview
Let's see what features are available in existing Oracle releases up to Oracle 11g Release 2.
There are different types of Auditing that you can perform at Oracle Database level. In general, auditing is performed to keep safe Database and to have better user control. It can also be used monitor any activities at Database level. For example: To monitor suspicious activity. At Database parameter level, we can use AUDIT_TRAIL, AUDIT_SYS_OPERATIONS and use package DBMS_FGA.ADD_POLICY for fine grained auditing.
2. Audit Trail Implementation Packages
Where Audits are Stored?
How Audit Data are Secured?
Audits are secured within the Oracle database at syslog audit: AUDIT_SYSLOG_LEVEL= local1.info
and by using Oracle Audit Vault.
3. Basic Audit Information (BAI) vs Extended Audit Information (EAI)
4. Extended Audit Information (EAI)
EAI is from SYS object view (SYS.UNIFIED_AUDIT_TRAIL) that has columns like FGA_POLICY_NAME, DP_TEXT_PARAMETERS1, DP_BOOLEAN_PARAMETERS1, RMAN_OPERATION, RMAN_OBJECT_TYPE, RMAN_DEVICE_TYPE, RMAN_xxx, OLS_POLICY_NAME, OLS_xxx, DV_xxx
5. Fine Grained Audit (FGA) Policy
FGA policy is added by using package DBMS_FGA.ADD_POLICY and any changes are recorded in UNIFIED_AUDIT_TRAIL which can be queried.
6. Data Pump Audit Policy
Audit policy can be created at Data pump using component datapump.7. Sample UNIFIED_AUDIT_TRAIL Query
8. RMAN Audit Information
Audit policy can be created at RMAN level by flushing the audit data using object SYS.DBMS_AUDIT_MGMT.FLUSH_UNIFIED_AUDIT_TRAIL.
9. Database Vault Audit Policy
Audit policy can be created at Database Vault using component dv. Any configuration changes at Database Vault can be audited.10. OLS or RAS Audit Policy
Oracle Label Security (OLS)
Real Application Security (RAS)
Audit policy can be using component OLS.
11. Unified Audit Implementation (UAI)
Unified Audit Implementation can be achieved using UNIFIED_AUDIT_TRAIL and uniaud_on binary.
12. Security Challenges - Roles
Packages like DBMS_AUDIT_MGMT can assist with AUDIT_ADMIN (Audit Administration) challenges. AUDIT_VIEWER can get UNIFIED_AUDIT_TRAIL views. AUDSYS is a dedicated schema at Database level.

13. Security Challenge - SYS Auditing
Non Unified Audit gets recorded in OS audit directory and Unified Audit can be performed at SYS.UNIFIED_AUDIT_TRAIL.14. Simplicity Challenges - Audit
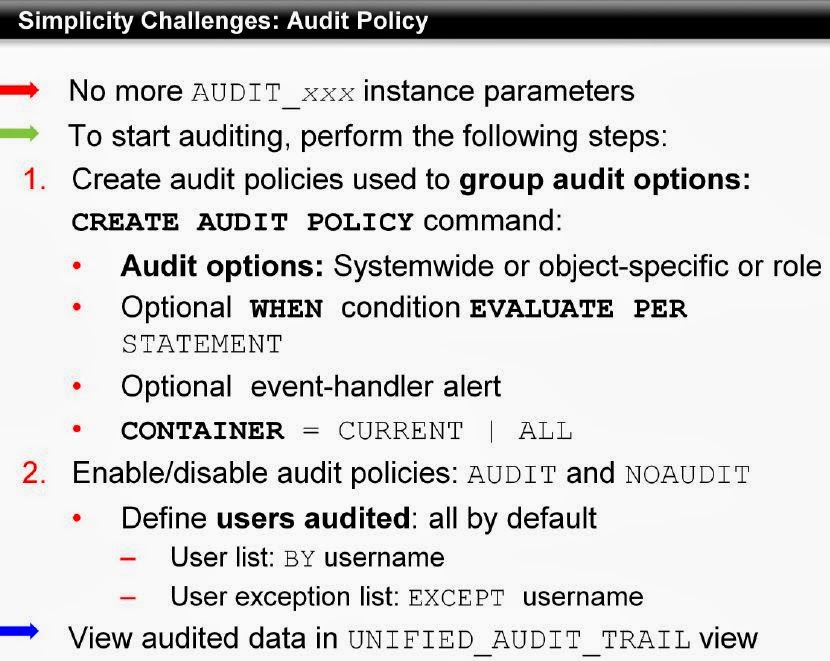
No longer need parameters like AUDIT_xxx. Audit policies can simply be created using CREATE AUDIT POLICY command and viewed at UNIFIED_AUDIT_TRAIL.
15. Steps to Create AUDIT Policy (STEP 1)
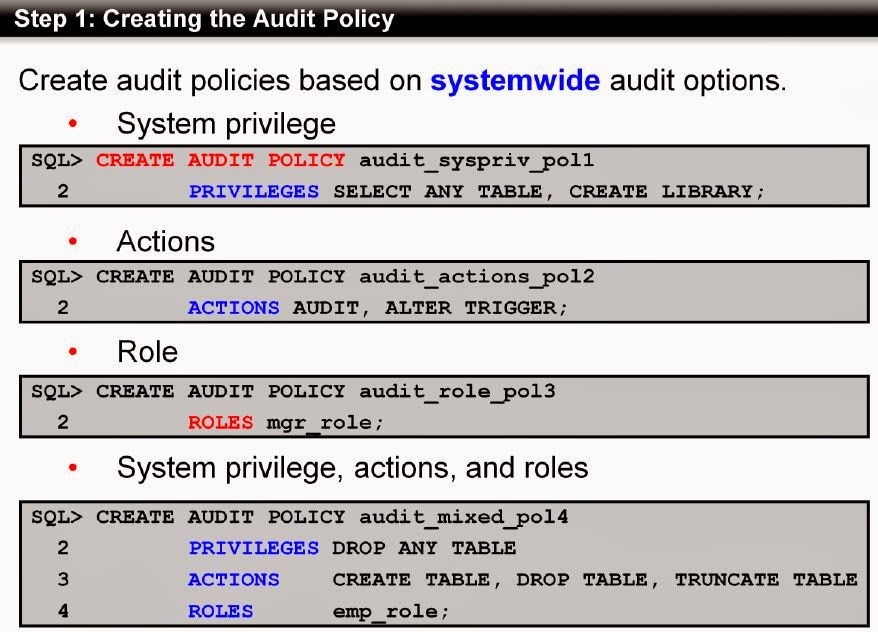
Using 'Create Audit Policy' command, create system privileges, actions, roles individually or all in one command.
16. Creating Object Specific Actions
Using 'Create Audit Policy' command, you can also create object-specific actions such as LOCK on a specific table or executing a grant on a specific object (For example: PL/SQL Procedure or Package).
17. Creating Audit Policy - Condition and Evaluation
Using 'Create Audit Policy' command, you can also add Conditions and Evaluations per session, statement and instance basis. Actions e.g., RENAME, ALTER on a particular Table.
18. Steps to Create AUDIT Policy (STEP 2)
To enable or to disable the audit policy. AUDIT POLICY Command can be used to enable or disable the audit policies.19. How to view Audit Policy?
Use views like AUDIT_UNIFIED_POLICIES and AUDIT_UNIFIED_ENABLED_POLICIES.20. Predefined Audit Policies
Policies like ORA_ACCOUNT_MGMT, ORA_DATABASE_PARAMETER, ORA_SECURECONFIG can be used to check on different audit options.Auditing Requirements
Commonly used auditing requirements are done for compliance and certifications reasons. Regulatory bodies with common auditing requirements:
Sarbanes-Oxley Act (SOX)
Health Insurance Portability and Accountability Act (HIPAA)
Financial Services Agency (FSA)
Payment Card Industry (PCI)
Data Security Standard (DSS)
Personally Identifiable Information (PII)
International Convergence of Capital Measurement and Capital Standards: a Revised Framework (Basel II) (ICCM) (BCBS)
Bank for International Settlements (BIS)
Japan Privacy Law / Japanese Hitoshi
Japanese Requirement Sarbanes-Oxley Act Section 302 (JSOX) Management Certification
European Union Directive on Privacy and Electronic Communications EU (DPEC)
Reference / Read More
1. Oracle Database 2 Day + Security Guide
12c Release 1 (12.1)
E17609-15
Chapter 9 Auditing Database Activity
http://docs.oracle.com/cd/E16655_01/server.121/e17609/tdpsg_auditing.htm
2. Oracle Database Security Guide
12c Release 1 (12.1)
E17607-19
Chapter 21 Introduction to Auditing
and
Chapter 22 Configuring Audit Policies
http://docs.oracle.com/cd/E16655_01/network.121/e17607/auditing.htm
3. Security Inside Out, Plug into Defense-in-Depth with Oracle Database 12c
https://blogs.oracle.com/securityinsideout/entry/plug_into_defense_in_depth
https://blogs.oracle.com/securityinsideout/

















It's interesting that many of the bloggers to helped clarify a few things for me as well as giving.Most of ideas can be nice content.The people to give them a good shake to get your point and across the command.
ReplyDeleteeSignature